Traefik Enterprise Edition on OpenShift¶
Traefik Enteprise Edition (TraefikEE) is a production-grade, distributed, and highly-available routing solution built on top of Traefik.
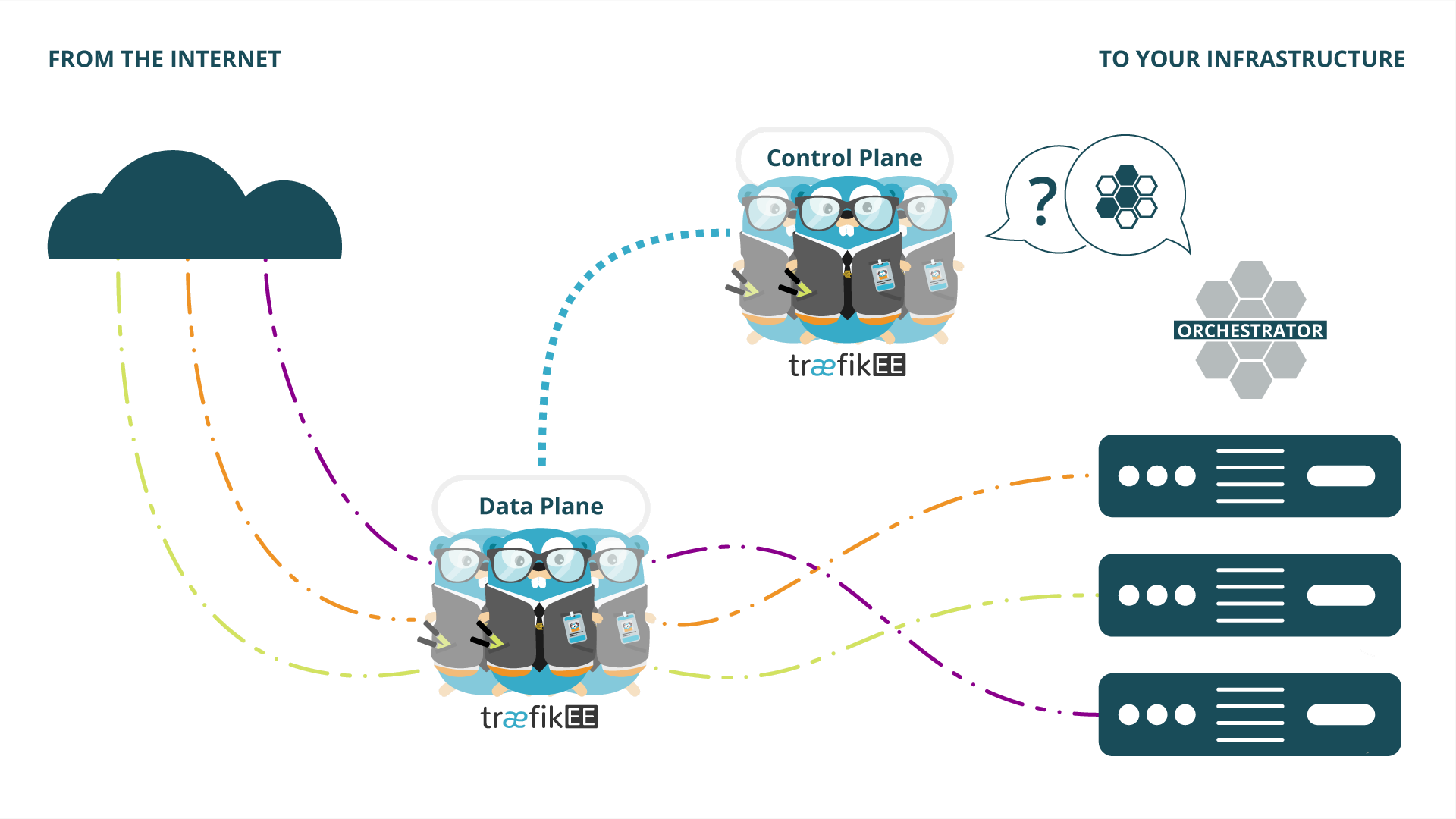
If you want to learn more about TraefikEE, please refer to the page "Concepts" of the documentation.
Prerequisites¶
This solution guide was tested with the following elements:
- OpenShift: 4.1.7, with the
ocadmin tools from openshift-client - TraefikEE v1.1.6, with the command-line tool
traefikeectl - A valid TraefikEE license stored in the environment variable
$TRAEFIKEE_LICENSE_KEY cluster-adminprivileges to manage Security Context Constraint- Access to the Kubernetes API with
kubectl, with the ability to create and manage namespaces and their resources
Preparing OpenShift¶
From OpenShift version 3.0 onwards, Security Context Constraints give the ability to a cluster-admin to control permissions for pods.
However, because the default Security Context Constraints does not allow binding privileged ports (under 1024), a custom one is required in order to install TraefikEE.
Security Context Constraint¶
Here is an example of Security Context Constraint a cluster-admin can set to a user/Service Account/Group.
---
apiVersion: security.openshift.io/v1
kind: SecurityContextConstraints
metadata:
annotations:
kubernetes.io/description: traefikee-scc provides all features of the restricted SCC
but allows users to run with any UID and any GID.
name: traefikee-scc
priority: 10
allowHostDirVolumePlugin: false
allowHostIPC: false
allowHostNetwork: false
allowHostPID: false
allowHostPorts: false
allowPrivilegeEscalation: true
allowPrivilegedContainer: false
allowedCapabilities:
- NET_BIND_SERVICE
defaultAddCapabilities: null
fsGroup:
type: RunAsAny
groups:
- system:authenticated
readOnlyRootFilesystem: false
requiredDropCapabilities:
- MKNOD
runAsUser:
type: RunAsAny
seLinuxContext:
type: MustRunAs
supplementalGroups:
type: RunAsAny
users: []
volumes:
- configMap
- downwardAPI
- emptyDir
- persistentVolumeClaim
- projected
- secretAdding the Security Context Constraint to OpenShift:
kubectl apply -f ./traefikee-scc.yamlOne Line Installation Requirements¶
Helm is used by the traefikeectl binary and must use a custom Security Context Constraint.
Example¶
# Create ServiceAccount and ClusterRoleBinding
echo 'apiVersion: v1
kind: ServiceAccount
metadata:
name: tiller
namespace: kube-system
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: tiller
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-admin
subjects:
- kind: ServiceAccount
name: tiller
namespace: kube-system'| kubectl apply -f -
# Init helm and tiller with the created ServiceAccount
helm init --service-account tiller --upgrade
# Add Security Context Constraint named traefikee-scc
kubectl apply -f traefikee-scc.yaml
# Replace restricted Security Context Constraint by traefikee-scc for tiller ServiceAccount
oc adm policy add-scc-to-user traefikee-scc system:serviceaccount:kube-system:tiller
oc adm policy remove-scc-from-user restricted system:serviceaccount:kube-system:tiller
You can then follow the Kubernetes One Line Installation procedure.
Yaml (Advanced) Installation Requirements¶
The user deploying TraefikEE must have the right Security Context Constraint.
Example¶
# Add Security Context Constraint named traefikee-scc
kubectl apply -f traefikee-scc.yaml
# Replace restricted Security Context Constraint by traefikee-scc for my-user User
oc adm policy remove-scc-from-user restricted my-user
oc adm policy add-scc-to-user traefikee-scc my-userThen, follow the TraefikEE on Kubernetes with YAML, either for Single Control Node or Multiple Control Nodes clusters.